In today’s digital world, owning cryptocurrencies like Bitcoin, Ethereum, and thousands of others comes with exciting opportunities — and serious risks. Cybersecurity threats, exchange hacks, and phishing scams are everywhere.
To truly secure your digital assets, relying on an exchange wallet or a mobile app is not enough.
The safest solution is a Trezor hardware wallet.
This guide explains why using a Trezor device is essential, how to set it up properly, and how it compares to other options like the Ledger hardware wallet.
What is a Trezor Hardware Wallet?
A Trezor hardware wallet is a physical device that stores your cryptocurrency private keys offline.
Unlike online wallets or apps that can be hacked remotely, a hardware wallet keeps your sensitive information disconnected from the internet, making it nearly impossible for hackers to access your funds.
Trezor, developed by SatoshiLabs, was the first hardware wallet ever created and remains a global leader in cryptocurrency security.
Key features of a Trezor hardware wallet include:
- Secure offline storage of private keys
- Easy integration with desktop apps like Trezor Suite
- Protection against malware, keyloggers, and phishing
- Support for thousands of cryptocurrencies
- Transparent, open-source software
Whether you are storing Bitcoin, Ethereum, stablecoins, or NFTs, the Trezor hardware wallet gives you complete control over your assets.
Why Choose Trezor Over Software Wallets?
Many beginners start with mobile apps or exchange wallets because they are convenient.
However, these solutions expose your crypto to internet-based threats.
A Trezor hardware wallet, on the other hand, offers:
- Total offline security
- Ownership of your private keys
- Immunity from exchange failures or hacks
- Advanced passphrase protection
Simply put, if you do not control your private keys, you do not fully control your cryptocurrency.
The Trezor hardware wallet puts the power back into your hands.
How to Set Up Your Trezor Hardware Wallet
Setting up a Trezor hardware wallet is easy, even if you are new to crypto.
Here’s how it works:
Step 1: Unbox and Connect
Unpack your Trezor device and connect it to your computer via USB.
You will be directed to install Trezor Suite and Trezor Bridge to begin the setup process.
Step 2: Install Trezor Suite
Trezor Suite is the official software used to manage your crypto securely.
You can download it onto your computer for maximum security and privacy.
Trezor Suite allows you to:
- Send and receive cryptocurrencies
- Manage your entire portfolio
- Access staking options
- Adjust privacy settings with tools like Tor integration
Step 3: Install Trezor Bridge
During setup, you will also install Trezor Bridge.
Trezor Bridge allows secure communication between your hardware wallet and the web-based or desktop Trezor Suite.
Without Trezor Bridge, your device would not be able to interact with your computer safely.
Step 4: Create and Secure Your Recovery Seed
The most important part of setup is creating your recovery seed.
You will be shown a series of 12, 18, or 24 words. Write these words down on paper — never save them digitally — and store them safely.
This recovery phrase is the only way to recover your funds if your Trezor is lost or damaged.
Step 5: Start Managing Your Crypto
Once your wallet is initialized, you can start sending, receiving, and storing cryptocurrencies securely using Trezor Suite.
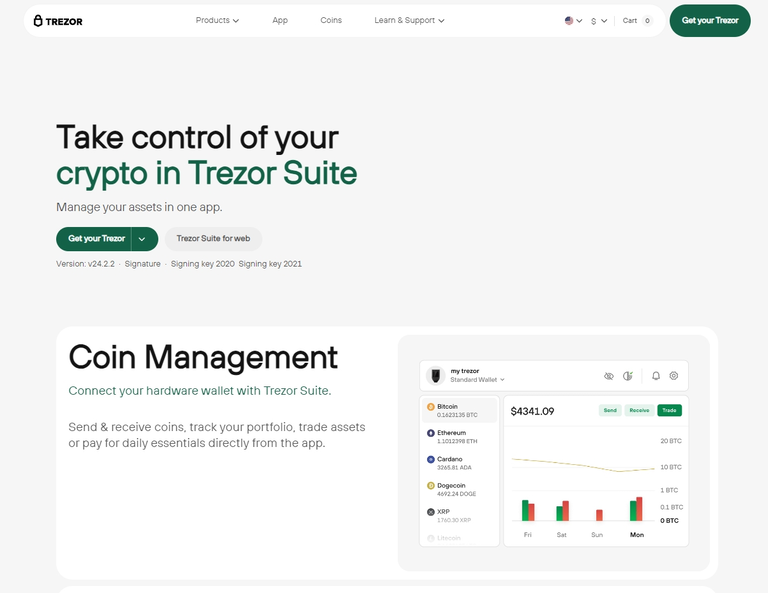
Exploring Trezor Suite: Your Crypto Management Dashboard
Trezor Suite is designed to make managing your crypto assets simple yet extremely secure.
Some of its standout features include:
- Support for a wide variety of coins and tokens
- Advanced transaction options
- Real-time portfolio tracking
- Customizable privacy settings
- Direct integration with decentralized applications (DApps)
Trezor Suite also helps you interact with DeFi platforms safely and manage NFTs stored on Ethereum or other blockchains.
What is Trezor Bridge and Why It Matters
Trezor Bridge is the software that acts as a communication link between your Trezor hardware walletRe and your computer browser.
It runs in the background and ensures that any transaction or device authentication request is handled securely without exposing private keys.
Keeping Trezor Bridge updated ensures your device remains compatible with the latest browser and system updates, keeping your crypto safe.
Trezor Staking: Earn Passive Rewards Safely
Staking has become an attractive option for crypto holders to earn rewards by supporting blockchain networks.
With Trezor staking, users can safely delegate their crypto while keeping full control over their private keys.
Although Trezor does not offer direct staking features in Trezor Suite for every asset yet, you can connect your Trezor hardware wallet to trusted staking platforms to participate securely.
Coins like Cardano (ADA) and Tezos (XTZ) are commonly staked using third-party integrations that work alongside your Trezor wallet
| Trezor.io/start | Trezor.io/start | Trezor bridge | Trezor suite | Trezor staking | Trezor.io/start | Trezor suite | Trezor Hardware Wallet | Trezor.io/start | Ledger hardware wallet | Ledger.com/start | Trezor staking | Trezor suite | Trezor Hardware Wallet | Ledger hardware wallet |


![[FAq~Fast] What is the Kraken Online Support Number?](https://bioneerslive.org/wp-content/uploads/2025/04/cryptoTRPzirQ-270x162.jpg)